“I had heard it was less secure, but I had no idea it was THAT insecure.”
This was the reaction given to Wavelynx’s sales engineer, Nate Doepper, after a short 30-second demonstration showed just how quickly he could clone the security manager’s access credential. Doepper has heard many reactions since he began giving these demonstrations, ranging from nervous amusement to “this can’t leave the room, my job is on the line.”
The access credential in question used proximity, or ‘prox’, technology, and to Doepper, it’s critically important to show just how insecure it is. In fact, as he puts it: “Prox credentials aren’t just less secure, they’re completely insecure.” That reality poses a major risk for organizations still relying on the outdated technology. And while credential cloning may seem like something only tech pros or experienced hackers could accomplish, the reality is anyone with $20 dollars and an Amazon account can make it happen.
According to VMR’s Global Access Control Report, 45% of businesses still use outdated systems more than 10 years old—and it’s not uncommon for an organization’s leadership to be unaware they’re at risk. Fortunately, as more organizations run through annual security audits, are educated by integrators, or learn the hard way with a breach—awareness of the dangers of legacy access control is steadily growing.
To better understand the issue, let’s take a deeper look at proximity cards, and why your organization’s employee badges could be a significant security risk.
The cost of prox cards in the real world
We’ve heard plenty of prox stories over the years. From college IDs cloned to steal meal plans, to apartment building cards duplicated for year-round pool access. In November 2024, a student at UNC made headlines after being arrested for using an RFID copier to clone key fobs, gaining access to restricted areas of campus.
While the severity of each incident may vary, the risk that a security breach could compromise your organization’s data, or more importantly, your people’s safety, is always present.
According to the IBM Cost of a Data Breach Report 2025, the average cost of a data breach in 2025 was $4.4 million dollars. Meanwhile, Verizon’s 2025 Data Breach Investigations Report found that credential abuse was the leading cause of breaches, factoring into 22% of cases. And depending on your industry, new and increasing security compliance requirements may carry fines of up to $50,000 per violation. Ultimately, with prox offering zero protection against card cloning, upgrading from the legacy system isn’t just a best practice to avoid fines, it’s urgent to protect your people, data, and reputation from an avoidable disaster.
What are prox cards?
Whether you call them access credentials, employee badges, or key cards, prox (or proximity) cards are contactless access control cards that transmit a unique identifier (essentially a password) to a card reader. What makes prox different from modern badges, however, is that it transmits data at the low frequency of 125 kHz.
Higher frequencies allow for faster data transfer and higher power capability, and with modern smart credentials operating at 13.56 MHz (more than 100x faster), prox cards simply don’t have the technical capability to support complex chips and memory-intensive cryptographic operations. In the world of security, prox is essentially like trying to use a computer of the 80s, floppy disks and all, for your current job.
Why are prox cards insecure?
- No encryption: Operating at 125 kHz, prox cards do not have the power and memory to support encryption. Without encryption, when your prox card transmits data to the reader, it essentially copies and pastes the exact “password” needed for entry. Unfortunately, this exact password is also what an RFID copier reads, and sequentially writes, onto a new blank prox card.
With encryption, a credential would transform that “password” into a series of seemingly random data before sending to a reader or RFID copier. While a reader would be equipped with the encryption key needed to convert the encrypted data back to the original password, an RFID copier would never be able to make sense of it, leaving your credential secure and unbreachable.

- Easy to clone: As we mentioned, without encryption, any RFID copier can read your prox card’s data. Unfortunately, RFID copiers aren’t sophisticated devices found on the black market, they can be found and purchased on Amazon for less than $20. The reality is that access to your facility or secure data is just an overnight delivery away.
>>> Don’t believe it? Watch this video where we purchase an RFID copier and learn to copy a prox card for the first time. <<<
Card cloning becomes even more insidious in the hands of a professional hacker with advanced tools. While most RFID copying devices require close proximity to read the data on a prox card, a skilled attacker can boost the signal on their RFID copier, allowing them to steal badge data from a concealed backpack several feet away. You’d have no idea it even happened as you were leaving your office.
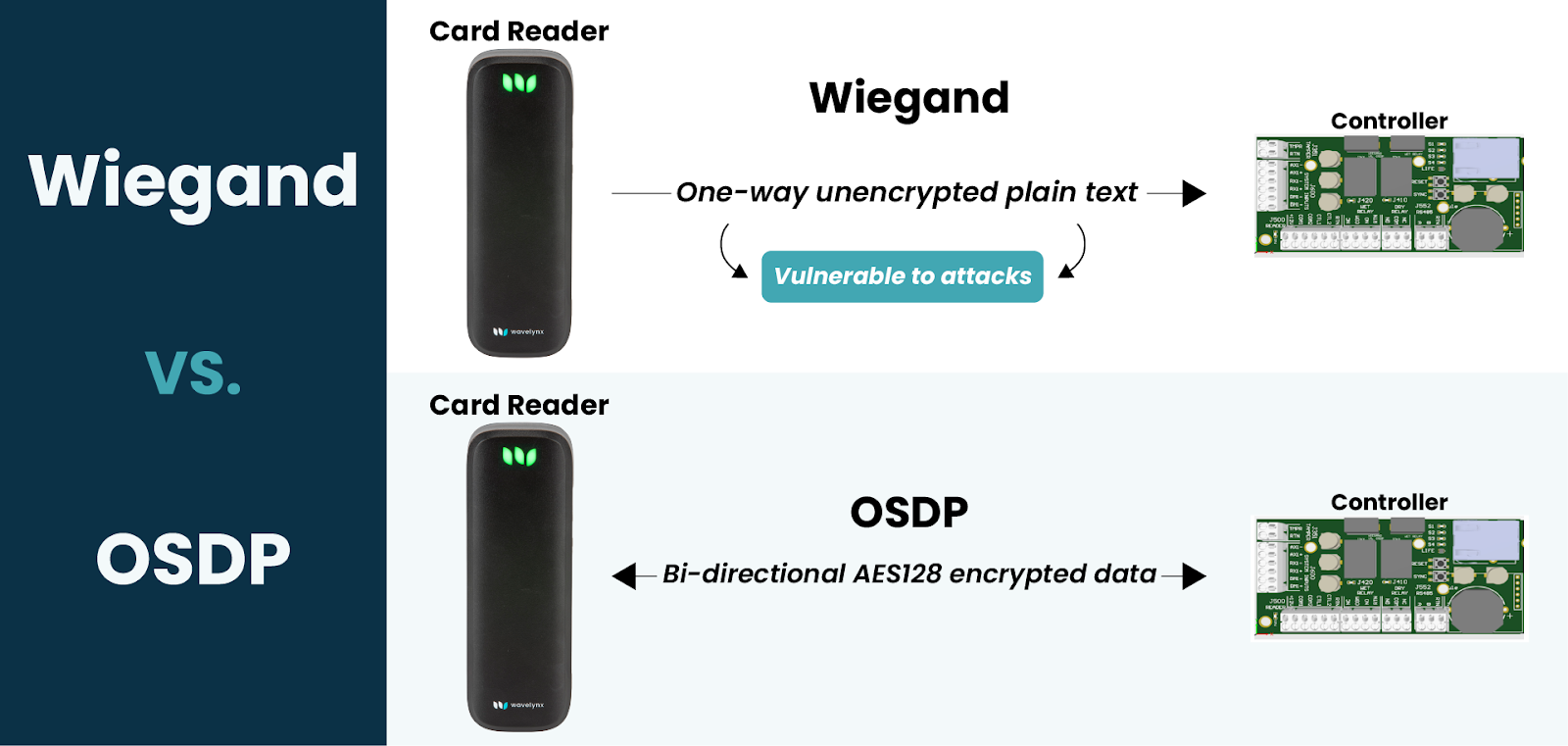
Hopefully you’re lucky enough to never experience such a breach, but in the world of high-cost security events, relying on luck can be a dangerous game. - Your prox card system is likely on Wiegand: After your card reader gathers a credential’s data, it sends it to your system’s controller. As the “brain” of the system, a controller processes credential information, references it against your network’s software, and makes the decision whether or not to provide access.
Connecting the reader to the controller is a wiring system that falls under one of two categories: OSDP—an encrypted modern system, or Wiegand—an unencrypted legacy system.
If your reader and credentials are legacy, then it’s likely your wiring system is too. Wiegand wiring sends your badge data from the reader to the controller in unencrypted plain text. Even if you’ve upgraded from prox, after the reader uses its encryption key to decipher the badge data, that data is still vulnerable as it travels to the controller.
While it takes more effort to place a reading (sometimes called “sniffing”) device along the wiring in the wall, it’s still a vulnerability you should consider when upgrading your system. Learn more about the differences between Wiegand and OSDP.
- Downstream attacks: If you’re upgrading your prox system in a phased approach, you may be using dual-tech credentials that support both prox and DESFire EV3 (Smart) technologies. Unless you’re utilizing a feature like Wavelynx’s Prox Filter, the prox side of your dual-tech credential will remain vulnerable until you’ve configured each one of your new readers to no longer read prox.
It’s technical, but the key takeaway is this: understanding the vulnerabilities and transition tools available (like Prox Filter) is critical as you build your plan to move away from prox.
The move from prox doesn’t have to be difficult
Depending on the size of your organization, you may be looking at replacing hundreds—if not thousands—of readers, and far more credentials. You may need to upgrade from Wiegand to OSDP. You may need new software and controllers. You may have multiple geographic locations that all need to transition. And you’re probably wondering if it’s possible to tackle all of these challenges without disrupting operations.
The world of access control is complex, but with the right plan, a smooth and simplified transition is absolutely possible. The key is understanding your options and phasing your transition in a way that ensures you’ll never experience operational downtime.
To better understand the various paths you can take, we recommend downloading the free guide: “Leaving Outdated Security Behind”. In this guide, you’ll learn:
- The access control ecosystem
- Credentials types and emerging technologies
- Features to consider when building your system
- The four primary transition strategies
- Hidden costs and how to avoid them
The bottom line on prox cards
As Nate wraps another card cloning demonstration, he looks up to see another nervous expression. His goal isn’t to elicit fear, but rather to inspire action. The mission is simple: make sure everyone using prox understands how crucial it is to upgrade from legacy technology.
“Just having credentials and readers can lull you into a false sense of security, but I’ll say it again, prox isn’t just less secure, it’s completely insecure, and if people know that I after I talk with them, then I’m doing my job.”
As security technology advances rapidly, so too do cyber threats. In a world where quantum computing, hacking techniques, and physical hardware evolve daily, there’s no place for a system first developed in the 1980s. Today, if you asked where to find a floppy disk, the answer wouldn’t be Fortune 500 offices—it would be antique shops and museums. We hope that soon the same will be said for prox cards.
Don’t wait until a breach puts your business at risk:
>>> Learn more about the dangers of proximity cards
>>> Download our free Transition Guide






.png)